Adding vendor-specific DNS records to Cloudflare
Adding DNS records for vendors
This article requires prior knowledge of DNS record management via the Cloudflare dashboard. To learn more, refer to Cloudflare’s article on managing DNS records.
Add the following MX records:
| Name | TTL | Record Type | Priority | Target |
|---|---|---|---|---|
| @ | Auto | MX | 1 | ASPMX.L.GOOGLE.COM |
| @ | Auto | MX | 5 | ALT1.ASPMX.L.GOOGLE.COM |
| @ | Auto | MX | 5 | ALT2.ASPMX.L.GOOGLE.COM |
| @ | Auto | MX | 10 | ALT3.ASPMX.L.GOOGLE.COM |
| @ | Auto | MX | 10 | ALT4.ASPMX.L.GOOGLE.COM |
Once added, the DNS records appear similar to the following in Cloudflare’s DNS app:
Test the Google Apps email configuration.
Add a CNAME record for Google App Engine to Cloudflare DNS.
For example, if the domain is www.example.com, the CNAME record is similar to:
www CNAME ghs.googlehosted.comTo configure a redirect for a Google Apps domain, refer to Google’s guide on URL forwarding.
Amazon
Amazon Route53
AWS customers must update their domain’s nameservers to point to the Cloudflare nameservers listed in the Overview app of the Cloudflare dashboard:
- Log into AWS.
- Click My Account in the top-right of the navigation bar.
- Select AWS Management Console from the dropdown.
- Click Services and select Route 53.
- Update nameservers in two places:
Click Hosted zones and select the domain to update with Cloudflare’s nameservers.
Edit the nameservers to point to Cloudflare’s nameservers.
Click Registered domains.
Select the domain to update with Cloudflare’s nameservers.
Click Add or edit name servers.
Amazon S3 bucket
Consult Amazon’s documentation on how to create an Amazon S3 bucket.
Note the full host URL assigned to the bucket.
Add a CNAME record for the AWS bucket in Cloudflare DNS. For example, if the full host URL of the bucket is files.example.com, add a CNAME record similar to the following:
files CNAME files.example.com.s3.amazonaws.comRefer to Amazon’s documentation about SES and verification settings.
Find the TXT and CNAME verification records that Amazon provides.
Add the records to Cloudflare DNS. For example, if the Cloudflare domain is example.com, the DNS records are similar to the following:
example.com TXT "fmxqxT/icOYx4aA/bEUrDPMeax9/s3frblS+niixmqk="verificationstring._domainkey.example.com CNAME verificationstring.dkim.amazonses.com Amazon ELB configuration
Refer to Amazon’s ELB help content for guidance on ELB configuration at Amazon.
- Add a CNAME record to Cloudflare for the hostname; for example: elb
- In the Cloudflare DNS app, replace Domain name with the ELB target: _
. ._elb.amazonaws.com is the proper CNAME target format (for example: _my-cool-cachepp-1344276401.eu-west-1._elb.amazonaws.com). - Reach out to AWS support to determine AWS hostname or region.
Microsoft
Follow Microsoft’s instructions on configuring Azure DNS settings.
Add Azure’s required records to Cloudflare DNS.
For example, if the domain is example.com, the record format is similar to:
example.com A 203.0.113.1www.example.com CNAME example.azurewebsites.netFor verification records, refer to Azure’s documentation on creating domain verification records.
Miscellaneous vendors
You can configure Cloudflare to work with ClickFunnels. The process requires updating your Cloudflare DNS settings.
The following articles from ClickFunnels outline how to best configure the two services for your site:
Refer to the examples below for adding proper Zoho DNS records to Cloudflare. In all examples, replace example.com with the actual domain name:
- Add Zoho MX records:
example.com MX mx.zohomail.com (set Priority to 10)example.com MX mx2.zohomail.com (set Priority to 20)- (Optional) Add an SPF record:
example.com TXT v=spf1 mx include:zoho.com ~all- (Optional) To access mail through a custom Zoho URL, add a CNAME record:
mail CNAME business.zoho.com- (Optional) To add a Zoho domain validation record:
zb******** CNAME business.zoho.comTypically, the DNS records are similar to the list below. Replace example.com with the actual domain name:
email CNAME sendgrid.netexample.com SPF v=spf1 a mx include:sendgrid.net ~allexample.com TXT v=spf1 a mx include:sendgrid.net ~allmtpapi._domainkey.EXAMPLE.com CNAME dkim.sendgrid.net.smtpapi._domainkey.e.EXAMPLE.COM CNAME dkim.sendgrid.netRefer to Ning’s documentation on Custom Domains and DNS entries.
If the Ning custom domain is www.example.com, add a CNAME and an A record as follows:
www.example.com CNAME example.ning.com.example.ning.com A 208.82.16.68After Ning verifies the domain, change the grey-cloud icon to an orange-cloud for the Ning DNS records so traffic can proxy to Cloudflare.
Consult SmugMug documentation for the latest details on DNS record requirements. Typically, add CNAME records for SmugMug similar to the following:
photo CNAME domains.smugmug.comphotos CNAME domains.smugmug.comAfter SmugMug verifies the domain, change the grey-cloud icon to an orange-cloud for the SmugMug DNS records so traffic can proxy to Cloudflare.
Refer to Mandrill’s article on DNS records for the latest details on DNS record requirements.
Mandrill requires addition of SPF and DKIM records. Obtain the DNS record values from Mandrill.
Add the SPF and DKIM records as TXT records in the Cloudflare DNS app.
For example, if example.com is the Mandrill domain, add DNS records similar to the following.
example.com TXT v=spf1 include:spf.mandrillapp.com ?allmandrill._domainkey.example.com TXT v=DKIM1\; (values from Mandrill)Configure Rackspace CloudFiles via CNAME record. Consult the Rackspace documentation.
Confirm the correct CNAME target with Rackspace support.
An example CNAME record appears as follows:
rack CNAME e0978.r18.cf2.rackcdn.comAfter ensuring that your domain nameservers are set to Cloudflare,
- Log in to the Cloudflare dashboard.
- Click the appropriate Cloudflare account for the domain where you will add records.
- Ensure the proper domain is selected.
- Click the DNS app.
- Ensure that all four (4) A records and the
wwwCNAME from Squarespace are mark Proxied. - Ensure that the
verify.squarespace.comCNAME record is marked DNS Only.
If set up properly, your Squarespace DNS Settings page will now indicate that your ‘Settings contain problems.’ This is the expected behavior.
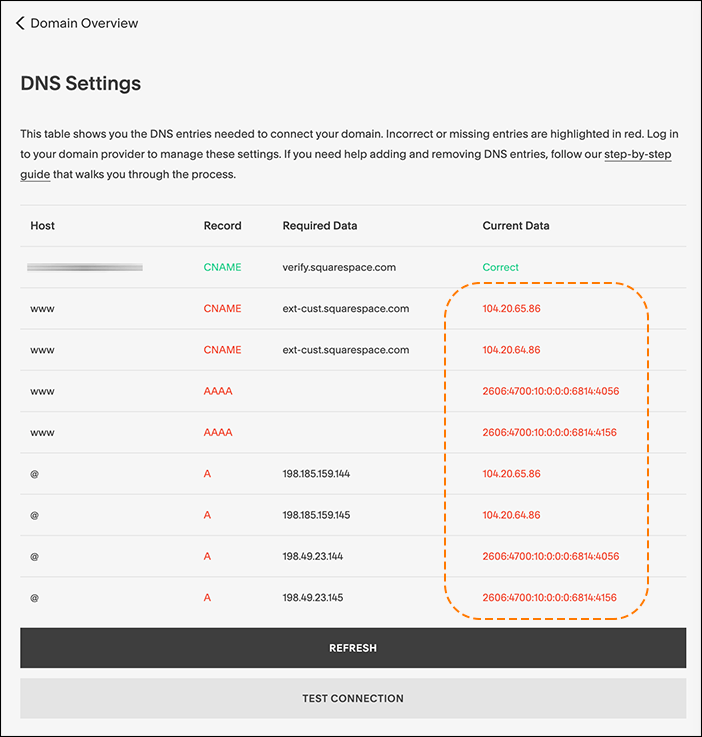
Now that your traffic is being sent through Cloudflare, Squarespace and your site’s visitors will see Cloudflare IP addresses. This causes Squarespace console to assume your site is misconfigured as Cloudflare IPs are returned instead of Squarespace assigned addresses. As long as you’ve configured Cloudflare DNS appropriately (above steps 1-6), your Squarespace site should now be working through Cloudflare.
If example.com is the custom domain, add DNS records to Cloudflare similar to these below:
example.com A 66.6.44.4www.example.com CNAME domains.tumblr.com