Skip inspection for groups of applications
You can configure Cloudflare Zero Trust to skip inspection for certain groups of applications.
Certain client applications, such as Zoom or Apple services, rely on certificate pinning. The TLS inspection performed by Cloudflare Gateway will cause errors when users visit those applications. To avoid this behavior, you must add a Do Not Inspect HTTP policy.
This walkthrough covers how to:
- Build a Do Not Inspect policy using Cloudflare’s list of certificate pinned resources
- Configure that policy’s precedence in your Gateway configuration
Time to complete:
5 minutes
Prerequisites
Build the policy
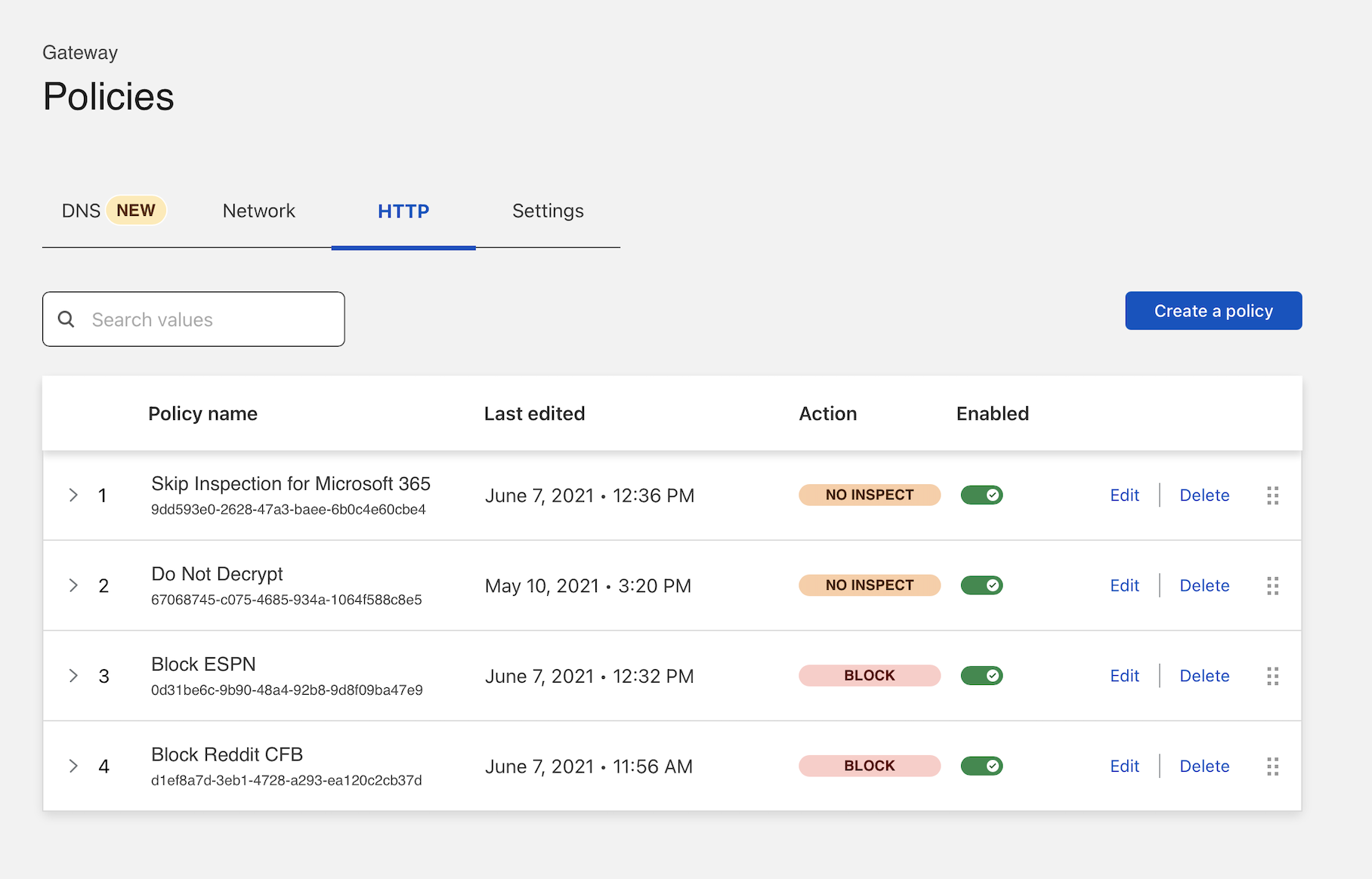
In Zero Trust, go to Gateway > Firewall Policies > HTTP. Select Add a policy.
Name the policy and, optionally, provide a description.
In the Selector field, choose Application. In the Operator field, select in. In the Value field, search for
Do Not Inspect. You can select either individual applications or the entire Do Not Inspect set, which will update as new applications are added.In Select an action, select Do Not Inspect. Select Create policy.
Change rule precedence
New rules are saved at the bottom of the rule list in Gateway. Gateway evaluates rules from top-to-bottom, except for Do Not Inspect rules. Those are always evaluated first. We recommend moving your Do Not Inspect rules to the top of the list to reduce confusion.
For more information, go to Order of enforcement.